How IBC is Trust-Minimized: Understanding Trust Assumptions in Interoperability
In the rapidly evolving world of blockchain technology, one challenge has consistently stood out: the need for effective and secure communication between disparate blockchain networks. This is where the Inter-Blockchain Communication Protocol (IBC) comes into the picture. IBC is a protocol suite that facilitates reliable, quick, and trust-minimized communication between heterogeneous blockchain networks.
The term "heterogeneous" is crucial here. Unlike homogeneous blockchain networks, heterogeneous networks can have entirely different architectures and consensus algorithms. IBC is designed to handle this complexity, providing a robust framework for cross-chain interactions.
In this article, we will discuss the IBC specification and architecture, provide a brief overview of how degrees of trust affect blockchain interoperability solutions, and conclude with an overview of Interchain Accounts, a novel application for inter-blockchain communication that goes far beyond simple token transfers.
A Brief History of IBC
The concept of the Inter-Blockchain Communicaton protocol isn't a recent development; it was a foundational element of the original 2016 Cosmos whitepaper. Indeed, right after IBC launched, many people called it the “Cosmos IBC” due to its launching along with the broader Cosmos ecosystem.
The idea behind the Cosmos whitepaper was to create a world of interconnected blockchain ecosystems, each with its own unique assets, smart contracts, and governance mechanisms. This vision has been a driving force behind the development of key technologies like the CometBFT consensus engine (formerly Tendermint Core), the Cosmos SDK, the Cosmwasm smart contracting platform, and of course, IBC itself. Today, these four technologies comprise the Interchain Stack.
The first implementation of IBC was launched in March 2021, marking a significant milestone in the journey towards a more interconnected blockchain landscape. Since then, the protocol has undergone various upgrades, each aimed at enhancing its capabilities and addressing the challenges that arise from real-world usage. Today, over 100 chains are IBC-enabled, and secures ~$40B USD in value transfers annually.
Understanding Trust in Interoperability Solutions
When it comes to cross-chain communication, the security of the interoperability mechanism is of critical concern. Generally, interoperability solutions can be categorized into three main groups based on how much trust is required in the system:
🗸 Trusted: Third party roots of trust (e.g., cross-chain bridges like Wormhole and Synapse Protocol)
🗸 Trustless: Sender & receiver share the same validator set (e.g., Ethereum <> Optimism native bridge)
🗸 Trust-minimized: Allows for blockchains with different validator sets to communicate without the need of a third party (e.g., IBC).
Trust-Based Interoperability Solutions
Trust-based interoperability protocols depend on third party roots of trust external to the two chains. Generally, trust in the security of the transaction is outsourced to a set of validators within the protocol's infrastructure. If you trust the validators, you trust the asset being transferred.
This design often incorporates additional security assumptions beyond a single set of external validators, such as relying on external entities like oracles or additional bridge validator sets. In all cases, there is an added security assumption of a third party in addition to the two original chains.
Trust-based interoperability protocols focus solely on verifying transactions between two different blockchain ecosystems. Common examples of these include cross-chain bridges like Wormhole and Synapse. The security challenges with trust-based interoperability are well-documented. A well-known example is the infamous Wormhole bridge hack in February 2022.
Some of the common security risks for trust-based interoperability systems include an exploiters targeting the smart contract that houses the tokens that have been transferred, exploits targeting multisignature wallets where bridge tokens are stored (code exploits and social engineering), and even validator collusion in bridge validator sets.
Unlike trust-based systems, trust-minimized protocols do not depend on third parties external to the chains involved in the transaction. The security model is inherently more robust because it doesn't introduce additional points of failure

The Inter-Blockchain Communication Protocol: A Trust-Minimized Interoperability Solution
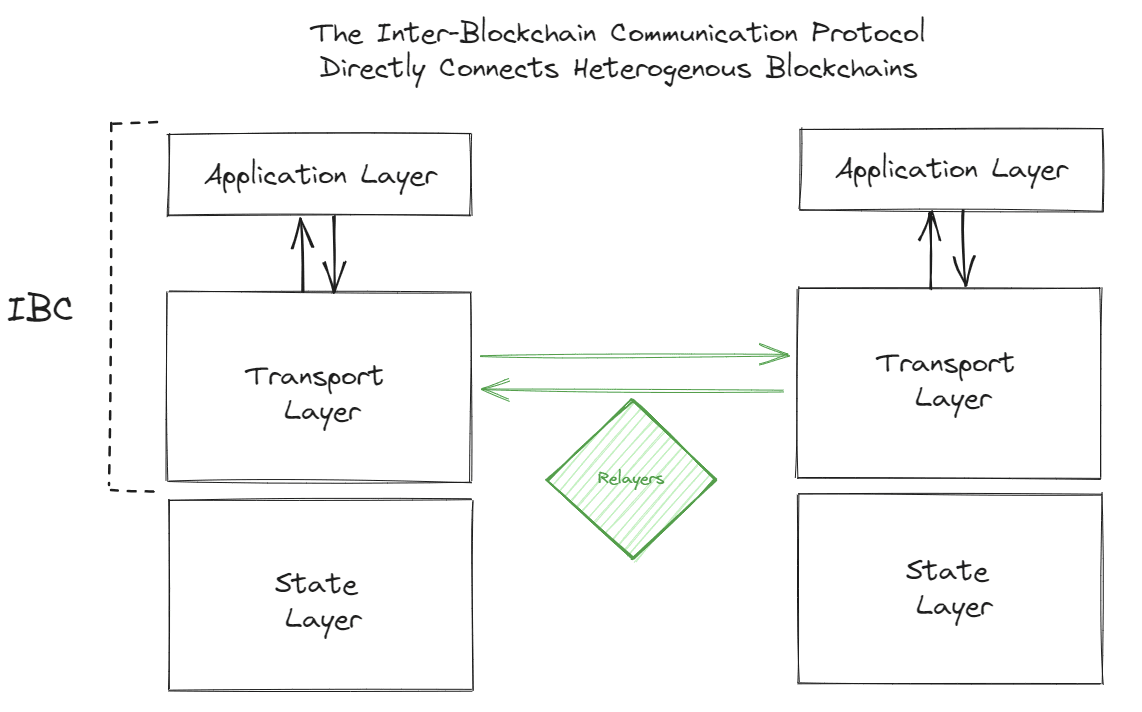
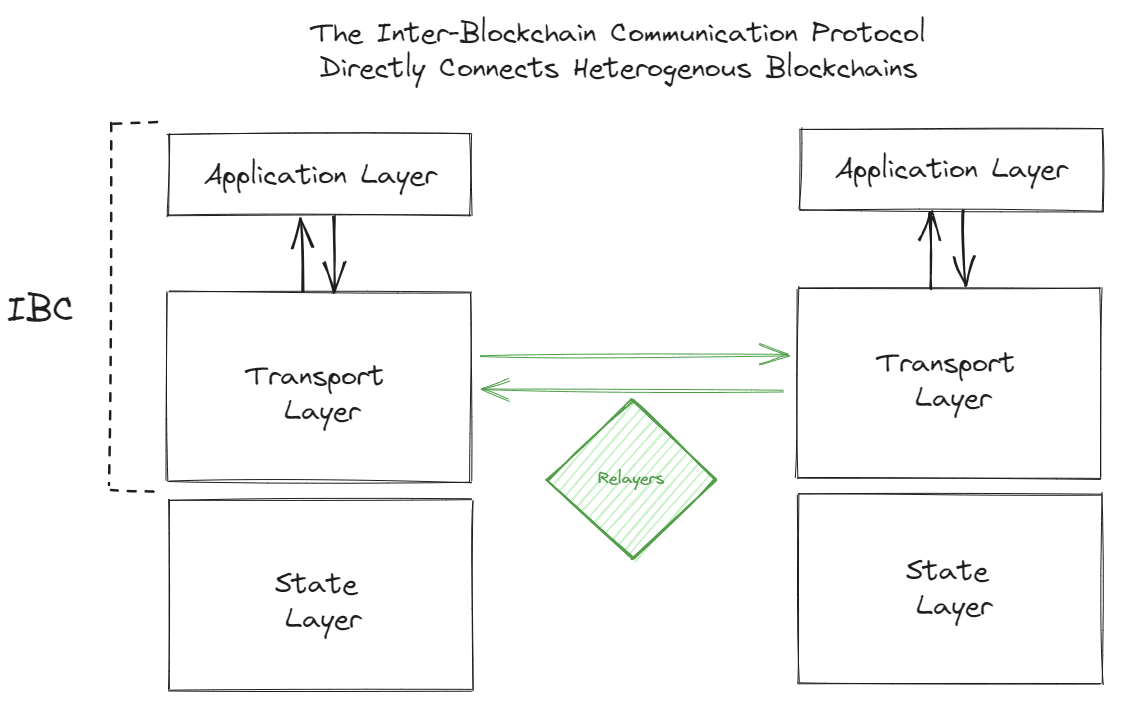
The Inter-Blockchain Communication Protocol, on the other hand, is designed as a trust-minimized system. This means that the two heterogeneous chains involved in the connection directly communicate with each other without an external third party acting as an intermediary to verify the transactions. They do this via light clients.
Before any cross-chain transactions occur, the IBC protocol sets up a connection between the sender and receiver chains. The protocol initiates a handshake, akin to the TCP/IP handshake, between the sender and receiver chain two chains that wish to communicate. Post-handshake, the light clients are able to verify the consensus of the counterparty chain by authenticating the Merkle proofs.. State verification is then performed within the light clients. Now, the two chains are directly connected without any third party in between.
For instance, the ibc-go implementation in the Cosmos SDK utilizes the Tendermint light client to validate state by verifying a Merkle proof against the latest consensus state of the counterparty chain.
How do IBC transactions work? Here's a quick summary.
First, a user (end user, smart contract, module, etc.) initiates a cross-chain transaction on chain A. This request is transmitted to the IBC Transport Layer to be sent to the receiver chain, chain B. At the transport layer, an off-chain process called a relayer carries the message from the sender to the receiver chain. Chain B uses its light client of chain A to verify chain A's consensus state & check that the transaction did occur. If the verification is successful, chain B will take the requested action on its chain.
This design eliminates the need for an external third-party validator, making the system more secure. The relayers that carry the messages between chains are agnostic to the data they carry, and cannot alter it; they're only responsible for transporting it. Furthermore, since chain B has a light client of A, it directly verifies A's consensus state. This means that there is no need for a third party trust assumption in this design, either via the transporting of the data or the verification. The receiving chain is able to directly verify the transaction on its own.
Finally, IBC's design is permissionless; any blockchain network can set up an IBC client and relayer and connect to other self-sovereign Interchain networks. It is not restricted to Cosmos-SDK based chains, either. Any chain ecosystem can connect through IBC if they have a light client, transport layer implementation, and relayer implementation.
Advantages of IBC's Design
IBC's architecture is layered, consisting of a transport layer for establishing secure connections and authenticating data packets, and an application layer that dictates how these packets should be processed and interpreted by the receiving chain.
The transport layer and the application layer work in tandem to ensure that cross-chain communication is both secure and functional. The transport layer provides the "highway" on which data travels, while the application layer defines the "rules of the road."
The design of IBC provides several advantages:
🗸 Security: IBC offers a robust security design, especially at the transport layer, due to its trust-minimized approach.
🗸 Generalized Data Transmission: IBC’s design allows it to pass any kind of data between chains. This allows for diverse and innovative interactions between chains that go far beyond standard token sends. One of these is Interchain Accounts - more on this below.
🗸 Flexibility and Versatility: The IBC protocol consists of base implementations ibc-go (in Golang) and ibc-rs (in Rust), and a composable suite of open-source modules that offer different functionality, allowing for endless creativity in development.
By prioritizing trust minimization, flexibility, composability, and sovereignty, the IBC becomes much more than just a method to transfer tokens. It instead becomes a superhighway for blockchain communication, where blockchains can leverage the best of their ecosystem for new business models, products, and infrastructure. In addition, the IBC modules are fully composable, and all are open-source.
Going Beyond Token Transfers: About Interchain Accounts
One of the most groundbreaking features of IBC is the introduction of Interchain Accounts (ICA). This module takes the capabilities of IBC to the next level by enabling a dynamic form of cross-chain interaction.
Interchain Accounts is possible due to IBC’s trust-minimized design. Since there are no third parties involved in the interchain communication, chains can directly and quickly send and receive messages.
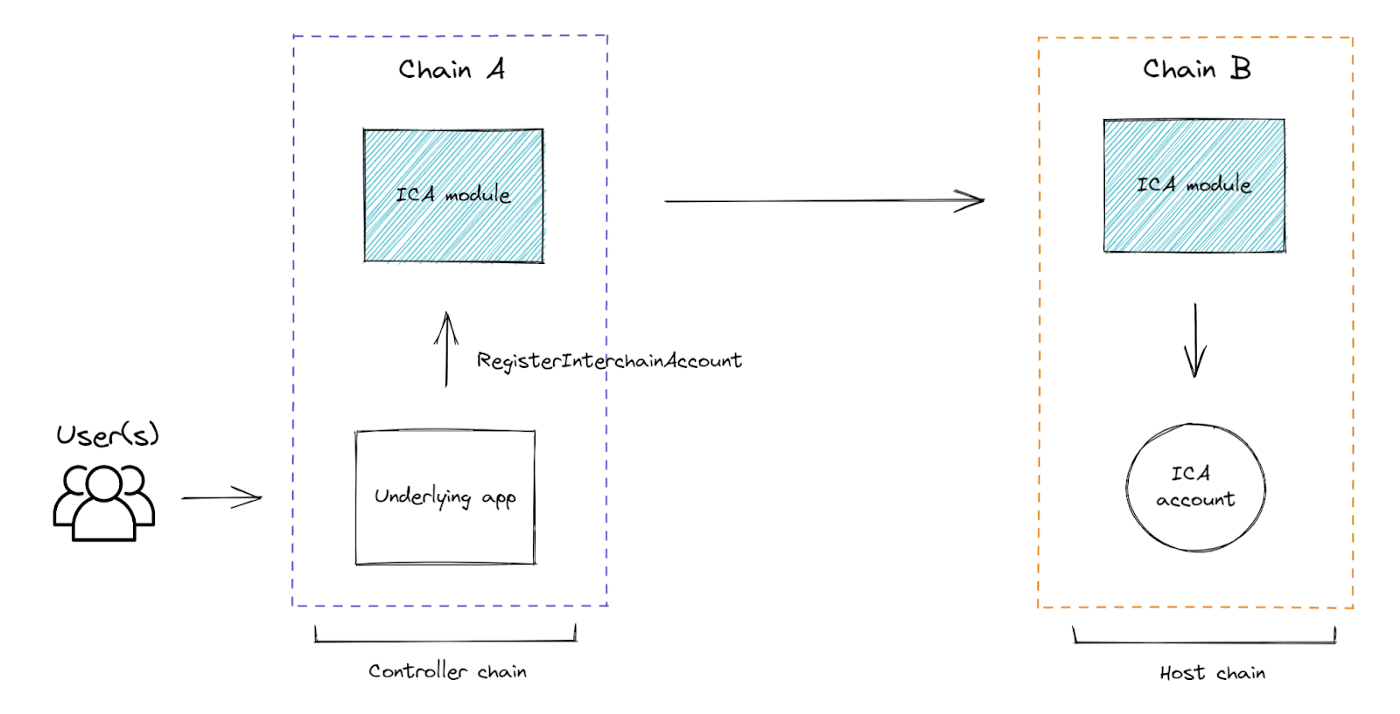
ICA enables Blockchain A to control an account on Blockchain B along a predefined set of messages, such as stake or burn. This allows for applications that were previously bound to a single chain to become native to the Interchain. The ability of one blockchain to modify the state of another blockchain is revolutionary in the context of blockchain interoperability.
How Interchain Accounts Work
An Interchain Account is essentially a container for transactions that can be executed on another chain. Think of it as a transaction within a transaction, or as it's often described, "a letter inside of an envelope inside of a box."
Before any ICA transactions happen on-chain, both the host chain & the chain controlling the account on the host chain (“controller chain”) have to enable the ICA module. This is done via a chain upgrade. Both chains will set an “allow list” of message types - such as send, stake, or burn - that can then be used for ICA transactions.
Interchain Accounts allows for a high degree of flexibility and composability. It enables transactions from application-specific chains to become their own composable primitives, thereby expanding the scope of what can be done across chains.
Concluding Notes
The Inter-blockchain communication protocol is revolutionary in its function, offering the most robust general-purpose message passing protocol to developers looking to build composable apps. The introduction of Interchain Accounts has further elevated this by allowing for complex cross-chain interactions that go far beyond token transfers.
By understanding the intricacies of IBC and the capabilities of IBC applications like Interchain Accounts, developers and blockchain enthusiasts alike can better appreciate the vast potential for innovation and integration in the blockchain ecosystem. The IBC protocol is not just a technological advancement; it's a paradigm shift in how we think about interoperability and cross-chain communication.



